
The Information Security, Cyber Insurance 2023 study explores the usage of cybersecurity insurance policies as a method of risk transfer for enterprise security programs, including the rise in premiums, the coverage offered, and the relative difficulty of coverage requirements.
The Take
Cyber insurance remains a sought after risk transference strategy for enterprise security leaders, but the market for acquiring insurance remains complex to navigate. Most of that complexity is due to the shift and growth in ransomware, from the opportunistic encryption of data and demands for payment for a decryption key, to focused multi-strategy monetized intrusions demanding eye-popping payments. The rise in such payments and related damages has led some insurance providers to decline to cover ransomware attacks, require specific attribution or declare certain attacks “acts of war” and thus outside coverage, or become increasingly specific about what’s covered. Some of these coverage issues will have to work their way through the courts as well, and that will take time. As an example, pharmaceutical company Merck only settled with insurance providers in 2023 regarding coverage for damages caused by the 2017 NotPetya attack.
Summary of findings
Forty-three percent of survey respondents representing the security organization within their enterprises report that cyber insurance is in place. Another 13% are in a discovery phase, while a further 13% intend to implement it within the next 12 months, so planned growth remains robust despite the reported challenges. Only 16% report that their organization has no plans regarding cyber insurance.
The majority (53%) of cyber insurance policyholders report that it is more difficult to meet the requirements of their policies than it was 12 months ago, and 15% say it is significantly more difficult. Only 6% say it has gotten easier to meet policy requirements. More than three-fourths (77%) of respondents note their policies require the implementation of specific information security tools. Policy premiums are also up for 78% of respondents, with an average 22% reported increase in premium. Only 13% of respondents kept their premiums flat year over year; CISOs who do so are starting to cite this as a professional competency. Methods that respondents employed to limit premium increases include implementing insurer-recommended security technologies (75%), providing more comprehensive answers to insurance questionnaires (38%), and allowing their IT provider to report directly to their insurance provider (25%). In fact, insurance requirements are directly affecting security vendor tool procurement: 15% of respondents say they already partner with a security product or service vendor that offers discounted third-party cyber insurance, while 77% say they would be somewhat likely (37%) or very likely (40%) to choose such a vendor.
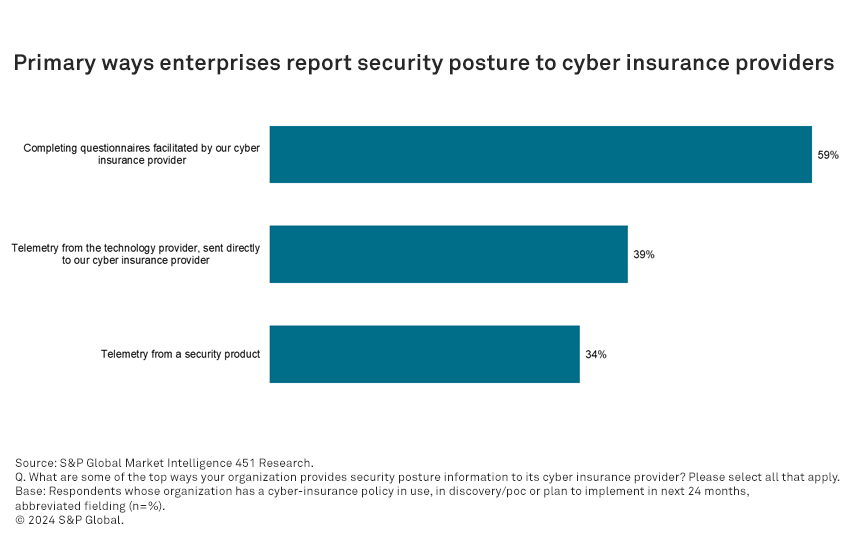
Questionnaires (59%) remain the most widely used tool to report cybersecurity posture to insurance providers. However, directly leveraging security telemetry is becoming more common, including data reported directly from a third-party technology provider (39%) or a security tool (34%).
Within the past year, about 15% of respondents submitted at least one claim against their cyber insurance, with mixed results. Among those who submitted claims, 54% say they fully recovered their damages on a claim, and 31% received partial coverage. Nearly a third (31%) report that a submitted claim was rejected because some aspect of the security incident did not fall under coverage parameters, and 23% had a claim rejected because the organization failed to meet a coverage requirement. Fifteen percent of respondents who filed claims found that a policy they thought would cover a cyber incident did not have such coverage — a warning to enterprise security managers to validate and ensure they understand the limits of current coverage before relying on insurance as a method of risk transfer.
Want insights on Infosec trends delivered to your inbox? Join the 451 Alliance.

