
Our Information Security, Identity Management 2023 study explores the types of authentication form factors in place at enterprises, notably including the percentage of applications that are still reliant on username/password combinations; the barriers to multi-factor authentication (MFA) adoption; and the steps enterprises take to reduce privilege escalation risk.
The Take
MFA continues to occupy a central role in implementing a zero-trust strategy — the top cited “important technology” for 39% of survey respondents, and the most cited response (55%) when security practitioners are asked what countermeasures they are taking in response to the privilege escalation that is common in ransomware and related intrusions. Despite that prominence in security planning, MFA is implemented at just 54% of enterprises overall. Within enterprises, an average of 37% of applications depend exclusively on usernames and passwords, with respondents citing user experience issues with MFA (33%), MFA setup costs (22%) and lack of support for MFA on legacy applications (16%) as reasons. SaaS applications with additional costs around MFA are derisively referred to as the “MFA tax” by practitioners, an attempt to move the de facto standard to including MFA without additional costs.
Enabling MFA (28%) and user experience with MFA (27%) are top pain points in identity management. Fatigue attacks against MFA, where an attacker continuously prompts MFA notifications until the legitimate account holder approves the request to make the alerts go away, have added a new wrinkle that has caused many enterprises to consider whether SMS-based (implemented at 42% of enterprises) or mobile push-based MFA (also 42%) are adequate as a second authentication factor due to susceptibility to this type of attack. Authenticator apps are implemented at 32% of enterprises, while other forms like USB keys (21%) and hardware OTPs (20%) persist.
Summary of findings
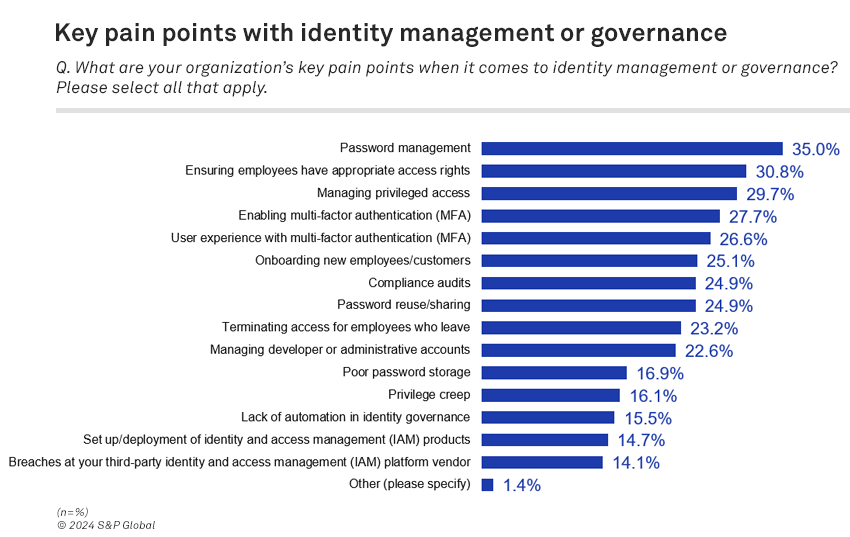
Password management is the most-cited identity management pain point (35%), slightly alleviated by usernames and passwords still being the most common form of authentication. Ensuring employees have the correct level of access (31%) — a form of the least privilege principle — and managing privileged access (30%) round out the top three most-cited concerns. Privilege creep, an issue effecting both concerns, is cited by 16% of respondents as a top pain point.
Privilege escalation is a common subsequent step for a bad actor who has gained internal access to an organization’s IT systems alongside lateral movement. Once a foothold is achieved, the attacker escalates vertically by trying to gain administrative rights or access to higher privileged accounts. As previously mentioned, the most common countermeasure enterprise security leaders say they use is MFA. Increased auditing (36%), implementing identity threat detection and response (36%), and periodic automated or manual review of permissions in active directory or Entra ID (35%) round out the top four most-cited responses by enterprise security leaders. Cloud infrastructure entitlement management implementation (30%) and privileged access management (26%) are also cited countermeasures.
Customer identity and access management allows for identity management, including authentication and authorization in use cases involving external identities. The most-cited reasons for implementing CIAM is to protect customer data (47%), but increasingly compliance with privacy requirements driven by regulatory concerns (39%) and improving visibility into customer activity (28%) also play a role. CIAM technology implementations are largely controlled by IT (65% of enterprises surveyed), but information security is also a significant stakeholder (35%).
Despite pronouncements from return-to-work advocates, the scale of remote work usage remains considerably elevated following the 2020 pandemic, with hybrid work emerging as a potential default. Security architectures have not entirely caught up yet, even some three years later: 25% acknowledge there are slightly more security controls in place inside a physical office, while 18% of survey respondents’ organizations have dramatically more controls in place for the in-office worker. Just 9% believe remote is now more secure.
Want insights on Infosec trends delivered to your inbox? Join the 451 Alliance.

