In response to the saying that every problem is an opportunity, a fellow 451 Research security analyst once joked that we have a ‘DDoS opportunity.’
Looking at the way the majority of respondents to our 451 Alliance survey who have encountered ransomware are dealing with it, ransomware may provide an opportunity.
The recent arrest of the security researcher who inadvertently shut down WannaCry, as well as the news that the authors of the ransomware have initiated the process of laundering their ill-gotten gains, are likely the closing salvoes of a 2017 security news cycle that have been dominated by ransomware. WannaCry knocked at technology services at a number of National Health Service hospitals in the UK among its 200,000 reported infections, and NotPetya, which may not even be ransomware in the traditional sense as it offered no way to unlock machines, hit the Ukraine particularly hard.
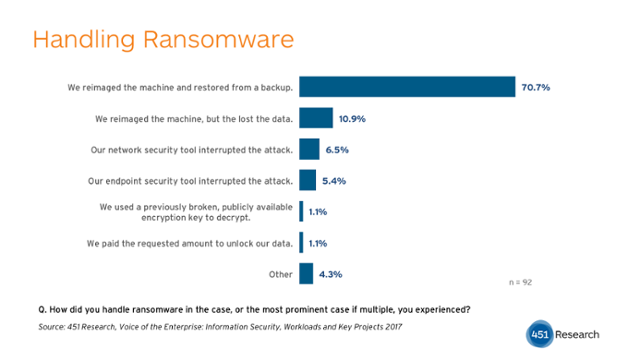
Despite the significant damage caused where infections were most prevalent, only 21.6% of respondents at the organizations surveyed noted being victims of ransomware in general. And of these, only 1.1% reported paying any ransom. The top response to dealing with a machine where all the files have been maliciously encrypted is, for most organizations, the same answer to dealing with any machine with a significant malware infection: It was pulled offline and reimaged. 70.7% of those who handled a ransomware infection were able to reimage the machine and fully restore from backup, 10.9% reimaged but lost data. In few cases, only 11.9%, did security tools interrupt and stop an in progress ransomware infection (some may have been blocked entirely by such tools before gaining a foothold).
For many organizations, this suggests that traditional good IT hygiene, having good backups, is going to be at least in the short term the not ideal, but for most good enough answer to ransomware. Thus the headlines can be turned to good cause if they provide an excuse, or better yet an opportunity, to push for testing that ensures backups are happening across the board and that the mean time to recovery (MTTR) for any continuity event is being held within acceptable bounds.
Or as one interviewee succinctly put it:
“We have had a couple of incidents of ransomware that we dealt with really handily, actually. It’s funny to me, because I hear horror stories about this ransomware stuff and organizations that are paying out.
I’ve had a couple instances now, and some of them have even gotten on the network, and they’ve encrypted a bunch of network files, and it’s like, “Okay. We pulled the machine off the network and I wiped it. And then I restored the files that got encrypted from backups and then that was it.” And less than a day later, we’re back to where we were.
I understand there are organizations that are way bigger, with what I suspect to be way more sophisticated operations that me seem to be having way more trouble with this. I don’t know if we just got lucky or if it truly is the case that we were better prepared.”
-IT/Engineering Managers and Staff, <250 Employees, $100m-$999.99m, Retail
