
The pandemic has shed light on many vulnerabilities and shortcomings about our global society, including our reliance on easily disrupted supply chains – remember the great toilet paper rush of March 2020? With the IT industry’s increasing reliance on third-party vendors, we’re coming to see that the industry is not immune to similar vulnerabilities.
With this increasing reliance on third-party vendors for services and software, management of IT environments grows more challenging by the day. Already, organizations are feeling the pain of trying to figure out the distinctions between a supplier’s obligations and their own in so-called ‘shared responsibility models’ of compliance and risk, particularly in resources hosted by third-party service providers.
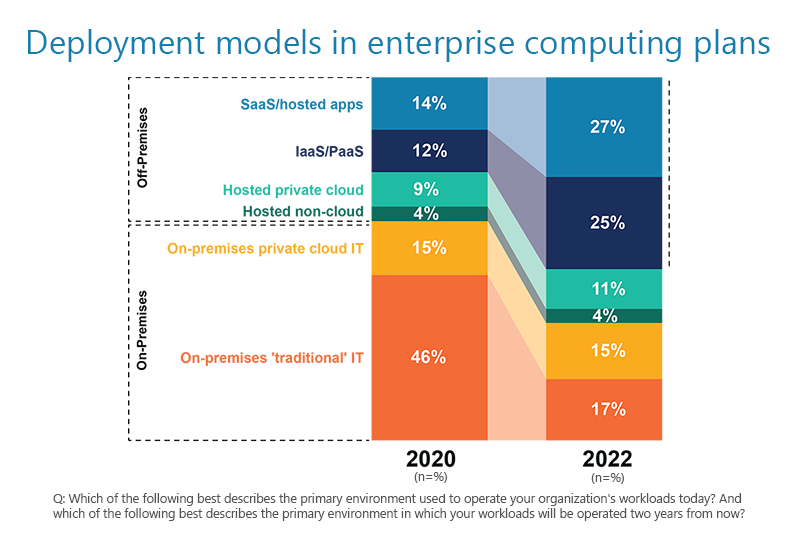
In a study conducted with the 451 Alliance, the variety of deployment models adds to the murkiness and various levels of indirection around an organization’s ‘own environment.’
Where does the responsibility of one party begin and another end?
Recent cyber security incidents, such as the attack on IT network management vendor SolarWinds, laid bare our industry’s reliance on supply chains that lead to vast interconnectedness.
In such cases, not only does the user of targeted products face exposure when its suppliers are compromised, but its own customers, users and other reliant parties may be exposed by its use of third-party offerings. And if those users, in turn, incorporate these same functionalities in their own offerings, they further risk having their own relying parties exposed.
The SolarWinds attack leveraged the routine process of software updates, a process the industry has encouraged organizations to follow, to keep software well maintained against (ironically) security threats, when, for example, new vulnerabilities are discovered. Technology providers have invested significantly in these processes, as a foundational aspect of keeping their products and customers secure.
The incident exposed some of the fundamental issues with risk visibility, particularly when it comes to risks introduced by third parties and in the IT supply chain. Our reliance on processes that have security measures in them that can be compromised beyond detection calls into question provider measures to mitigate risks to those processes. But if that’s the case, how much visibility will providers be willing to extend to relying parties to demonstrate the measures taken are enough, and have not also been compromised?
The vulnerability of the IT supply chain lies in existing techniques
Ironically, the SolarWinds compromise shows us the future of IT isn’t all we need to worry about. Weaknesses aren’t found only in newly developed platforms and technologies; existing technologies and techniques we’ve relied on for years have proven vulnerable as well. Given the depth, detail and daunting scale that is being faced by third-party cyber and IT supply chain risk management, we as an industry have our work cut out for us.
Get free research reports on technology trends when you join the 451 Alliance. See if you qualify.
