
Source: Dimitri Otis/Stone via Getty Images.
A recent study conducted by 451 Research, a part of S&P Global Market Intelligence examines the requirements driving extended detection and response, supporting technologies layered atop security analytics investments (such as threat intelligence), the important technologies for a security operations center, enterprise plans to implement generative AI in SecOps, and the key features that are considered when purchasing SecOps tools.
The take
The platform versus best-of-breed argument in the selection of security vendors is decades old, but significant players in the extended detection and response (XDR) market have recently reignited the debate in light of a perceived need for consolidation of security tools in organizations amid tightening economic conditions and increasing threat complexity. Some arguments for a platform approach — fewer vendors to manage, a single partner to hold accountable — seem to fall flat among buyers in the security space per prior survey research. But a limited number of agents, consolidated reporting from multiple tools and reporting that combines identification of problems alongside enforcement, while potentially providing an integration point where newer technology capabilities such as AI can act on data, do resonate with the security buyer.
SecOps is an area where the platform approach is being touted by providers, and this survey asks whether that viewpoint is taking hold among practitioners. Twelve percent of survey respondents do not have a primary SecOps vendor, leaving 88% who do. Among those organizations, 36% of SecOps spending goes to that primary vendor on average. For organizations with more than 1,000 employees, it is 40%. While this indicates the common presence of a single-vendor SecOps platform, it also indicates that platform is not capturing the bulk of spending today. Depending on one’s point of view, that could indicate that security teams implement limited platform-based approaches to SecOps or that there is significant opportunity for platform vendors to capture additional budget by displacing security point solutions.
Summary of findings
In the wake of a major availability incident with a popular security tool earlier this year, one question that arose for folks outside the security profession was why this type of security tool had become so ubiquitous in organizations. The key benefits of XDR, according to respondents, are around scaling SecOps capabilities (cited by 45%), providing higher-quality alerts in terms of correctness (lower false positives) and information provided for triage (44%), increased visibility (41%), and better guidance for SecOps personnel on how to respond (39%).
Respondents still note an average of 43% of security alerts from their SecOps systems go uninvestigated due to a lack of person power or available resources. These can be considered “known unknowns” (as opposed to problems that are not being alerted on at all), meaning there are indicators of a problem, but it falls below the priority threshold for the SecOps personnel available to dig into the issue. The percentage of alerts uninvestigated, security’s “dark data problem,” marks an improvement from last year’s 54%, and represents a change in the trend line as the percentage had been rising each year since 2020 when it was 37%.
Last year, 32% of surveyed security professionals thought generative AI could significantly impact SecOps — for example by simplifying the gathering and correlation of additional data related to an alert in an incident investigation. This year, 15% of respondents report using generative AI in their SecOps platforms, typically via a vendor-supplied solution that integrates with existing SIEM, XDR and additional tools, and that offers a prompt for inquiries, analysis of what a script or code is doing, or summaries of indicators of compromise that appear to be steps in a sequenced attack, alongside relevant third-party threat intelligence. Twenty-two percent of respondents report having pilots underway.
While branded socks remain a popular booth giveaway at the major security conferences, it is important to understand the metaphor they represent — the SOC (security operations center) is not universally present in organizations. Because of that, vendor use cases that assume the presence of an SOC and dedicated SecOps professionals as users can fall short in practical implementation. Sixty-five percent of organizations have an SOC in place, and that rises to 86% for large organizations with more than 1,000 employees. But only 53% of organizations with fewer than 1,000 employees report having any form of SOC in place. For vendors that sell into smaller-scale organizations, defining a SecOps solution’s value with a part-time operator who may not have a deep security background becomes important.
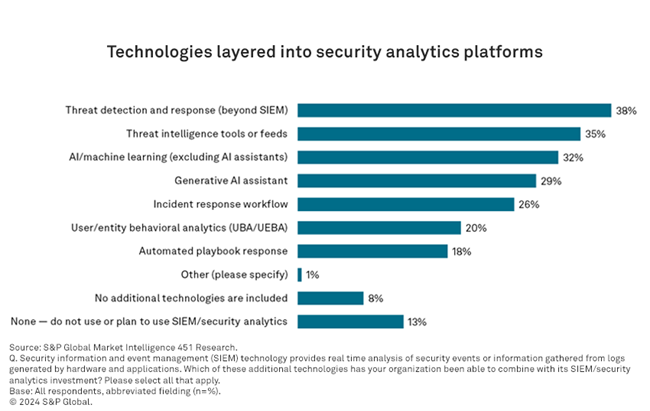
Threat detection and response tools are, at 38% of citations, the most common technology implemented on top of SIEMs or security analytics platforms. Closely following, at 35%, is third-party threat intelligence — platforms where outside information about security threats can be referenced against what is happening internally for applicability to a specific organizations’ environment’s context. Finally, 32% note that SecOps is a key integration point for the security team to leverage AI to identify patterns in available security data.
Want insights on Infosec trends delivered to your inbox? Join the 451 Alliance.
Want insights on consumer technology trends delivered to your inbox? Join the 451 Alliance.
This content may be AI-assisted and is composed, reviewed, edited and approved by S&P Global in accordance with our Terms of Service.
