
Source: key05/iStock/Getty images.
Operational technology environments are increasingly interconnected with information technology systems, creating new avenues for both innovation and vulnerability. A study conducted by S&P Global Market Intelligence 451 Research focused on IoT and OT security provides a snapshot of how organizations perceive risks, allocate responsibility for OT security, and prepare for the most pressing cyberthreats. While many organizations acknowledge the rising sophistication of adversaries and the persistence of ransomware, phishing and social engineering, the survey highlights a disconnect between perceived maturity and actual preparedness.
The Take
The S&P Global Market Intelligence 451 Research survey data highlights the mismatch between organizational confidence and real-world vulnerabilities.
Close to 40% of respondents consider their security posture well-managed and mature, yet findings show uneven automation of security processes and technology, limited resilience against phishing-driven attacks and inconsistent governance structures.
This overconfidence, when coupled with regional disparities in risk perception, suggests that organizations are still underestimating the true scale of operational technology (OT) security challenges.
Summary of findings
Network security continues to dominate as the foremost concern for OT organizations, with 54% of organizations identifying it as their top issue. Cloud security follows closely at 47%, while IoT endpoint and device security, as well as employee awareness, rank third at 43%. The results reaffirm a multiyear trend in which European organizations remain significantly more concerned about every aspect of OT security than their North American peers, demonstrating a consistently heightened sensitivity to cyberrisks in markets in Europe, the Middle East and Africa.

When it comes to governance, responsibility for OT security varies widely. For 44% of organizations, OT security remains under the umbrella of the general IT department. Another 31% have established dedicated OT security teams, while 22% outsource key OT security functions to managed service providers. This distribution reflects a sector still defining how to delegate in-house expertise and balance external support.
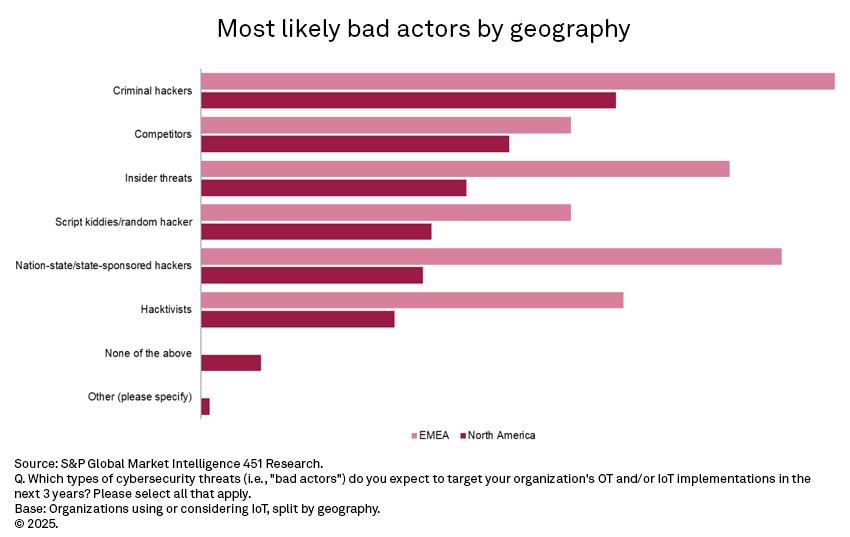
Criminal hackers continue to be viewed as the most likely adversaries, cited as a concern by 54% of organizations. Competitors and insider threats follow at 40% and 37% respectively, while globally, nation-state sponsored hackers are considered a threat by 30% of respondents. Regional differences remain stark: In Europe, 80% of organizations expect to be targeted by criminal hackers compared to just 52% in North America. Similarly, 73% of European organizations anticipate nation-state attacks, compared to only 28% of North American organizations. This wide gap mirrors patterns observed in previous years, suggesting that European organizations continue to view themselves as far more exposed to geopolitical cyberthreats.
Our data reveals that organizations expect to face ransomware and malware the most (45%), followed by identity-based attacks (33%) and vulnerability exploits of legacy OT devices (30%). In terms of delivery methods, phishing emails overwhelmingly stand out as the most likely vector, with 71% of respondents citing them as a top concern. CEO fraud is noted by 43% of organizations, an increase of 8% compared to 2024, while general social engineering remains a notable threat at 40%. Interestingly, only 3% of organizations regard deepfake technology as a credible social engineering threat, despite increasing global attention to AI-enabled deception.
Interestingly, there is a disconnect between how organizations assess their own security maturity and the reality of said security. Nearly 40% of organizations believe they maintain a well-managed security posture, with formal structures, compliance processes and monitoring mechanisms in place. Yet, as was true in our 2023 and 2024 surveys, the reality is far less robust. Despite optimism, the reality is that many OT environments remain exposed due to inconsistent levels of automation, insufficient network segmentation and inadequate protection for connected devices.
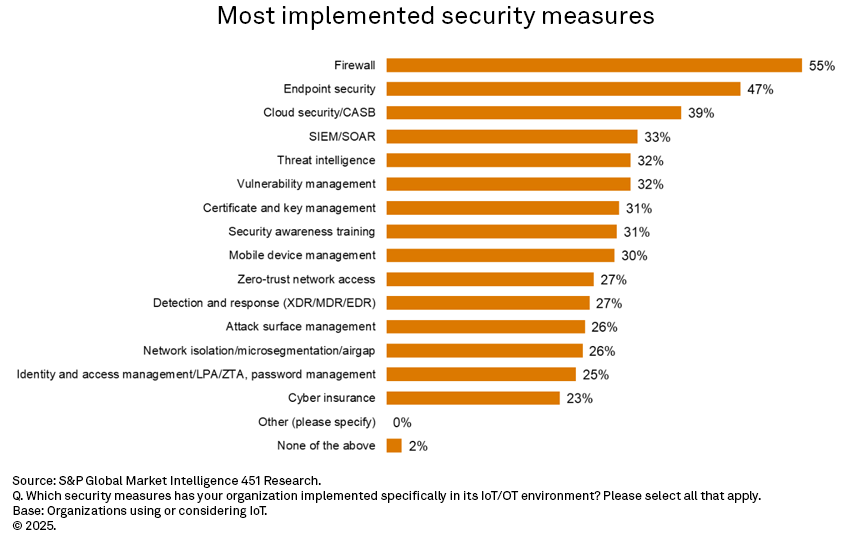
When looking at security in OT environments, the top five most implemented measures include firewalls, endpoint security, cloud security, security information and event management (SIEM)/security orchestration, automation and response (SOAR) and threat intelligence, but only 55% of companies cite that they have implemented firewalls, and only one in three indicate they have SIEM/SOAR and threat intelligence solutions in place for their OT environment.
The greatest challenge for security vendors remains educational, particularly in helping organizations recognize the true risks posed by the convergence of IT and OT, and the vulnerabilities inherent in connected OT systems.
Conclusion
The survey conducted by S&P Global Market Intelligence 451 Research underscores the paradox of OT security today: organizations are acutely aware of traditional threats such as ransomware and phishing, yet are overconfident in their ability to manage such threats. Regional differences highlight divergent perceptions of risk, with European organizations demonstrating much greater concern around nation-state and criminal activity than their North American peers. Moving forward, the challenge lies not only in deploying more advanced technical controls but also in aligning organizational perceptions with the realities of the threat landscape. Only by closing this gap can organizations hope to achieve true resilience in their OT environments.
Want insights on IoT trends delivered to your inbox? Join the 451 Alliance.

