Source: Carlina Teteris/Moment/Getty images.
A recently conducted study by S&P Global Market Intelligence 451 Research examines the security tooling organizations are using to enable monitoring, detection, investigation and response to potential security incidents. The study examines the attributes most frequently considered when purchasing SecOps tools, the integration of additional tooling around security information and event management to form SecOps platforms, and the emerging role of generative AI in security operations.
The Take
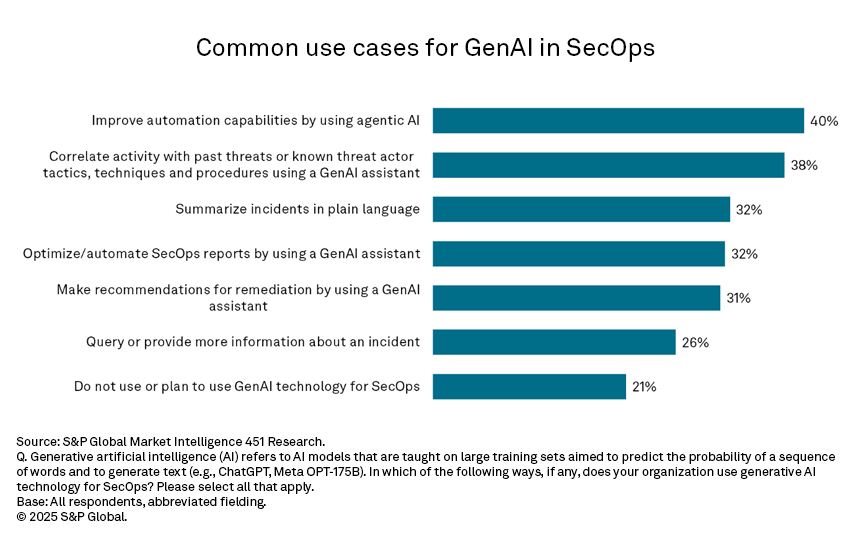
When asked to identify where generative AI capabilities are supporting security operations, practitioners most frequently cite automation via agentic AI (40%). Automating aspects of detection, analysis or response, including outside tool coordination and data retrieval, can streamline repeatable incident response tasks in chronically understaffed security operations centers (SOCs). A close second is using GenAI assistants to correlate current activity with past activity or known threat actor tactics, techniques and procedures (38%) — a key part of threat hunting. The remainder of the top five responses highlight efforts to boost efficiency in some of the most complained-about, time-intensive SOC tasks: summarizing incidents in write-ups, automating reporting, and making remediation recommendations.
Summary of findings
The most damning finding in the SecOps study over the past few years remains the percentage of alerts that SecOps staff are aware of and simply cannot address due to a shortage of person-power. In the 2025 study, the average proportion is 45%, steady with 43% in 2024 and an improvement over 2023’s 54%. This number helps explain the enthusiastic response to capabilities that automate important but repeatable tasks, as outlined in the paragraph above: Any improvement that allows for added investigation of known anomalous or problematic activity is likely to be welcomed. While correlation should not be confused with causation, one cannot ignore that GenAI tool integration accompanied the 10-percentage-point drop in average unaddressed alerts between 2023 and 2024, after years of continual increase.
In the 2025 study, generative AI assistants (44%) are the most commonly cited technology integrated into SIEM or security analytics, ahead of supplemental threat detection and response (38%) and threat intelligence tools (37%). As noted above, organizations are applying GenAI capabilities for a variety of purposes, led by agentic automation.
Nearly two-thirds of organizations surveyed (63%) report having a SOC in place. While nearly all organizations have some form of security operations, a SOC is a more formalized, centralized function that attempts to provide full-time monitoring for security events. Due to the staffing implications, SOC presence is highly dependent on company size. While 52% of companies with fewer than 1,000 employees have a SOC, the proportion rises to 84% among companies with more than 1,000 employees. It is also more common in highly regulated industries: 83% of financial firms and 78% of healthcare firms have a SOC, well above the overall average.
In the past two years, major information security providers have emphasized a move toward “platformization,” including via high-profile acquisitions. This trend is particularly pronounced with SecOps tooling, as users need multiple tools to work together in a smooth, integrated fashion, and also seek to lower switching costs, such as those associated with managing across multiple tool dashboards. This is exemplified in the earlier data point that considers how many different types of tools have been closely integrated into SIEM offerings over time. Whether that is achieved through the tight integration of products across multiple vendors or whether security buyers are safest working with a single primary vendor are all key buying considerations of security practitioners who have historically shown a “best of breed” acquisition bent.
Organizational security respondents on average report that they spend 32% of their SecOps tooling budget with a “primary” SecOps vendor, indicating that while there are certainly “base” vendors in a SecOps tool chain, they have not captured the majority of the available budget. Only 7% of practitioners say they don’t have a primary SecOps vendor, while just 1% say they have a single vendor, indicating that the vast majority use a combination of primary and secondary suppliers. There is a positive bent in reported satisfaction with an organization’s primary SecOps vendor. On a 5-point scale, where 5 is “excellent,” practitioners on average rate the usability of their primary SecOps tool as a 4. Meanwhile, 84% say that different products from their primary SecOps vendor are well integrated and function as a whole — the rationale behind a platform approach. The remaining 16% say that products appear bundled and not well integrated.
Want insights on Infosec trends delivered to your inbox? Join the 451 Alliance.