
Source: Ralf/Technology via Getty Images.
In the fast-paced world of technology, IT decision makers face the challenge of staying ahead while effectively managing the convergence of IT, operational technology (OT), and cybersecurity. A recent global IT outage, precipitated by CrowdStrike pushing a faulty content update to Windows hosts, has highlighted the paradox of success in these domains.
The immediate impact of the global IT outage revealed the following key issues: Firstly, the incidents affecting widely adopted providers can have a significant impact on customers and those dependent on them. Secondly, the impact extends beyond IT when OT has interactions or dependencies on IT and cybersecurity technology providers. The third issue is the fragility of systems, which must be addressed by the industry to reduce fragility and ensure greater resilience for digital technology going forward. When considering the risks associated with popular suppliers, buyers must assess the extent to which they can realistically mitigate these risks without sacrificing the advantages of working with a popular supplier.
Managing the challenges of concentrated technology risks
Without having to sacrifice the advantages of working with popular suppliers to, organizations must consider several factors:
1. Evaluate resilience: Assess the resilience of your digital technology infrastructure and identify potential vulnerabilities. Implement measures to improve resilience, such as network isolation, microsegmentation, or air gap measures.
2. Diversify providers: Consider diversifying your technology providers to reduce risk concentration. However, be cautious of relying on multiple providers with similar processes and techniques that could result in similar outages.
3. Comprehensive platform strategies: Choose between comprehensive platform strategies offered by major vendors or an architectural approach that reduces dependence on any one provider. Consider the advantages and disadvantages of each approach based on your organization’s specific needs.
Impact and mitigation
The impacts for vendors and their customers are intertwined. Vendors may face tangible consequences, such as questioned investments, as a result of the incident. On the other hand, customers must consider the cost of lost productivity and the resources required for remediation and recovery. Additionally, downstream impacts are likely to occur, particularly when critical business applications are affected rather than just IT office systems.
Airlines, for example, face flight cancellations and disruptions to automated boarding gates and baggage handling systems. Retailers may experience point-of-sale downtime, leading to a loss of sales. In healthcare, operational outages can result in delayed or deferred care. Organizations must prioritize the remediation and recovery of critical business applications to minimize the downstream impacts.
The intersection of IT and OT
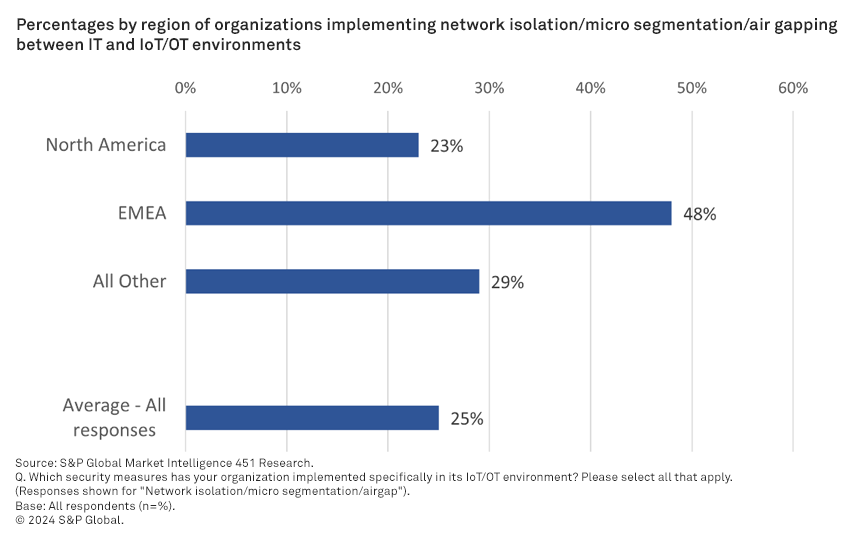
The incident also highlights the need for greater scrutiny of the intersections and dependencies between IT and operational technology (OT). According to a recent Technology and Business Insight report by 451 Research, a part of S&P Global Market Intelligence, only 48% of organizations in Europe, the Middle East, and Africa, and 23% in North America have implemented network isolation, microsegmentation, or air gap measures to prevent spillover from IT to OT environments. This event serves as a wake-up call for organizations to address these vulnerabilities.
Conclusion
Every organization will experience both the benefits and challenges associated with different approaches to IT, OT, and cybersecurity. For providers, these challenges are an inevitable part of their success. There is ongoing discussion about whether the major incident involving CrowdStrike and Microsoft poses an existential threat or will impact other successful providers. However, it is too early to speculate on the outcomes. It is worth noting that highly successful providers have already demonstrated their resilience in the face of such issues. The response of those involved in this case will undoubtedly shape the future outcomes.
In the current landscape, a platform’s success is at the forefront of many minds. This incident coincides with the security community’s preparation for major annual gatherings, such as Black Hat, DEF CON, and other conferences in Las Vegas, which are just a few weeks away. This timing adds significance to the discussions surrounding the incident and its implications for the security market.
Want insights on consumer technology trends delivered to your inbox? Join the 451 Alliance.
This content may be AI-assisted and is composed, reviewed, edited and approved by S&P Global in accordance with our Terms of Service.

