
Source: Petter Lagson/lagopett via Unsplash.
A recent study conducted by 451 Research, a part of S&P Global Market Intelligence examines the growth rate of specific identity technologies, key security pain points around identity, drivers for customer identity and access management, and inhibitors to the rollout of multi-factor authentication.
The Take
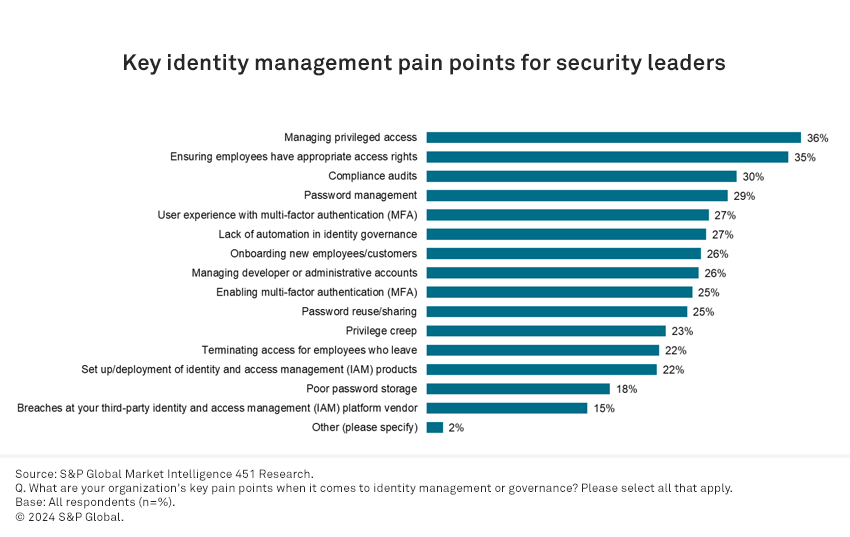
Managing privileged identities remains a headache for organizations’ security leaders — it is the top-cited pain point in identity management (36%). This result was likely predictable, as respondents to a prior survey also conducted by 451 Research, a part of S&P Global Market Intelligence, which focused on organizational behavior. IT staff with elevated privileges were the subject of greatest concern in that particular study. Most successful cyberattacks begin with bad actors gaining a foothold via intrusion, followed by an attempt to escalate privilege to enable lateral movement through an environment. Compromising privileged identities is often like stealing the keys to the kingdom. The 2022 Lapsus$ attack against Uber is a well-known example. It started with the attacker defeating multi-factor authentication via a fatigue attack — sending so many multi-factor authentication (MFA) requests that a legitimate user accepts one to get the messages to stop. After gaining entry, the attacker found credentials for Uber’s privileged access management tool in PowerShell scripts, gaining administrative access to multiple sensitive services. In general, privileged access management (PAM) tools protect privileged accounts by enforcing the principle of least privilege regarding “administrative” access, or the right amount of access to complete a legitimate job-related task at the right time with proper logging of actions in place. In the more recently completed study, which focused mainly on the different types of information security technologies, 13% of organizations stated they’re piloting PAM tools to manage privileged access, and an additional 16% plan to implement them in the next six months.
Want insights on consumer technology trends delivered to your inbox? Join the 451 Alliance.
Summary of findings
Beyond privileged access, ensuring employees have appropriate access rights is a pain point in itself, cited by 35% of respondents. Implementing a least-privilege approach is especially difficult in environments without a clear mapping of job roles to appropriate systems access, which makes onboarding new employees challenging — a key issue cited by 26% of respondents. Furthermore, 27% cite lack of automation in identity setup and provisioning as a key problem. “Privilege creep” (23%) becomes an issue as employees move between roles, sometimes retaining the access rights of a prior position while adding those of a new job.
Just over one-quarter (27%) note that user experience with MFA is a key pain point. This is particularly an issue when it inhibits the full rollout of MFA, as respondents also cite MFA as a key defense against ransomware attacks (57%). Respondents note that, on average, about 70% of applications in their organizations require more than just a password to login — a strong improvement over years past. However, there are also issues with the type of MFA implemented, as alluded to above when describing fatigue attacks. Key inhibitors to the full rollout of MFA include user experience issues (30%), setup costs (29%) and lack of support for legacy technology that is still in use (24%).
Ransomware is also a key driver of identity threat detection and response implementations. Ransomware resilience (44%) is the top-cited reason for ITDR adoption, followed by identifying excessive permissions (39%) and preventing privilege escalation or lateral movement (39%). Just over half (51%) of survey respondents say they have ITDR in place, an additional 16% have pilots underway and 11% plan to implement it in the next six months.
CIAM, which is concerned primarily with enabling customer access to business services, is reported in use by 44% of surveyed organizations, with another 18% piloting solutions. Protection of customer data (53%), compliance with privacy requirements (42%) and preventing creation of fraudulent accounts (34%) are driving that growth.
Want insights on Infosec trends delivered to your inbox? Join the 451 Alliance.

