
Source: ARAMYAN/Technology via Adobe Stock.
A recent study conducted by 451 Research, a part of S&P Global Market Intelligence, examines the prevalence of ransomware attacks, how organizations are responding in the moment and strategically in the longer term, trends in the number of tools and agents installed on endpoints, and use cases where endpoint security tools excel versus those where they fall short.
The Take
Upon seeing the percentage of survey respondents who experienced a ransomware attack fall from 23% in 2023 to 14% in 2024, one might think the problem of ransomware is slowly coming under control. After all, the eye-popping ransoms reported in 2022 are not filling headlines the same way in 2024. But media fatigue in reporting attacks does not negate significant attacks against a telecommunications provider, auto dealership software and a major healthcare provider this year, just to name a few examples. The most concerning finding this year is that, while fewer respondents reported attacks, a significantly larger percentage of affected organizations paid the ransom: 18%, up from 6% in 2023.
Summary of findings
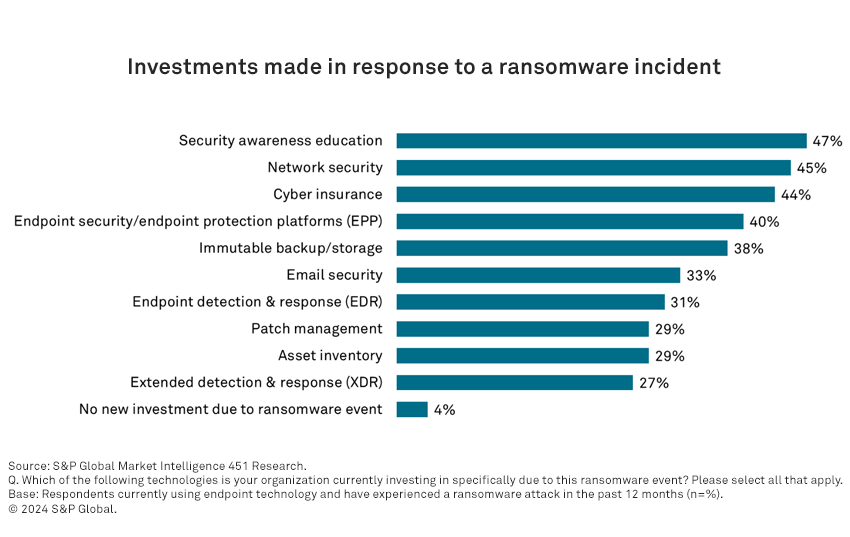
Overconfidence in security tooling remains an issue in the face of ransomware. Among respondents who have not experienced a ransomware attack in 2024, 34% believe their network security tooling would stop the attack, and 25% believe an endpoint security tool they have installed will interrupt the same. Among respondents who dealt with an actual attack, network security tools blocked 14% of the attacks and endpoint security was effective for 13% of respondents. The most common response to ransomware remains reimaging machines and restoring from backup (34%), indicating the importance of a resilience-based strategy focusing on backup technologies such as immutable storage — an investment subsequently made by 38% of respondents who experienced ransomware events. Focusing on risk transference through cyber insurance remains a key strategy cited by 44% of respondents, and 78% of those who experienced ransomware either purchased or extended a cyber insurance policy.
The mean number of endpoint security tools installed per endpoint is 3.04, a number that is fairly consistent with the results from 2023 (3.1) and 2022 (3.07), representing a post-pandemic hybrid and mobile computing environment that has put focus back on securing endpoints in the absence of reliance on office network security controls. The number of different tools, and agents, running on endpoints has long been a concern of security leaders as well as users due to performance issues, and 23% of respondents report that their organization is running more than five. The number of tools is also closely tied to an organization’s size: Organizations with fewer than 250 employees average 2.66 endpoint security tools per endpoint, whereas those with more than 10,000 employees average 3.65.
Respondents cite preventing the loading and execution of malware as the top effective use case for their endpoint security tools (48%), followed by detecting and stopping malware during or after execution (33%). About one in eight (13%) cite automatic removal of malware and post-attack remediation as a strength. When it comes to weaknesses, the greatest proportion cite facilitating after-the-fact investigations (24%). About one in six (17%) note their endpoint security tools are ineffective at automated remediation of malware’s effects. Leveraging external threat intelligence at the point of attack has been a key role of endpoint security as far back as primarily signature-based antivirus, but 13% say their endpoint security tool is weak in that capability.
Internet of things (IoT) and operational technology in industrial control systems represent endpoints with very different security requirements, and OT generally represents a more difficult target for attackers. That has not stopped significant attacks, in which motivated attackers have designed exploits to target specific systems and bridged attacks from IT to OT networks. When one considers a full IoT system, from the endpoint itself to its connectivity back to a control point, there are many potential points of attack, from breaking weak authentication on the device, to compromising its network traffic, or attacking systems that interact with multiple devices. Among these threats, attacks against a centralized control point (29%) rank first. Dealing with unpatched application security vulnerabilities (28%) ranks next — it is difficult to issue patches or fixes once devices are in the field.
Want insights on Infosec trends delivered to your inbox? Join the 451 Alliance.

